linux安全篇:禁止頻繁訪問(wèn)的ip訪問(wèn)nginx


點(diǎn)擊「閱讀原文」查看良許原創(chuàng)精品視頻。
點(diǎn)擊「閱讀原文」查看良許原創(chuàng)精品視頻。
實(shí)驗(yàn)環(huán)境
版本:redhat6.5
ip:172.16.1.100,172.16.10
軟件:nginx
172.16.1.10部署nginx
[root@localhost?tools]#?ls
nginx-1.11.2.tar.gz
[root@localhost?tools]#?yum??install?gcc?gcc-c++?make?automake?autoconf?libtool?pcre*?zlib?openssl?openssl-devel
[root@localhost?tools]#?tar?xf?nginx-1.11.2.tar.gz?
[root@localhost?tools]#?ls
nginx-1.11.2??nginx-1.11.2.tar.gz
[root@localhost?tools]#?cd?nginx-1.11.2
[root@localhost?nginx-1.11.2]#?ls
auto??CHANGES??CHANGES.ru??conf??configure??contrib??html??LICENSE??man??README??src
[root@localhost?nginx-1.11.2]#?./configure
[root@localhost?nginx-1.11.2]#?make
[root@localhost?nginx-1.11.2]#?make?install
<以上代碼可復(fù)制粘貼,可往左滑>
測(cè)試nginx服務(wù)
[root@localhost?~]#?curl?-I?172.16.1.100
HTTP/1.1?200?OK
Server:?nginx/1.11.2
Date:?Mon,?17?Aug?2020?09:36:29?GMT
Content-Type:?text/html
Content-Length:?15
Last-Modified:?Mon,?17?Aug?2020?09:36:19?GMT
Connection:?keep-alive
ETag:?"5f3a4f93-f"
Accept-Ranges:?bytes
<以上代碼可復(fù)制粘貼,可往左滑>
nginx 可以正常訪問(wèn)。
接下來(lái),假設(shè)172.16.1.100是黑客主機(jī),頻繁訪問(wèn)nginx服務(wù)
模擬172.16.1.100訪問(wèn)10次172.16.1.10
172.16.1.100
[root@localhost?~]#?ab?-c?1?-n?10?http://172.16.1.10/
This?is?ApacheBench,?Version?2.3?<$Revision:?1430300?$>
Copyright?1996?Adam?Twiss,?Zeus?Technology?Ltd,?http://www.zeustech.net/
Licensed?to?The?Apache?Software?Foundation,?http://www.apache.org/
Benchmarking?172.16.1.10?(be?patient).....done
Server?Software:????????nginx/1.11.2
Server?Hostname:????????172.16.1.10
Server?Port:????????????80
Document?Path:??????????/
Document?Length:????????612?bytes
Concurrency?Level:??????1
Time?taken?for?tests:???0.016?seconds
Complete?requests:??????10
Failed?requests:????????0
Write?errors:???????????0
Total?transferred:??????8450?bytes
HTML?transferred:???????6120?bytes
Requests?per?second:????617.02?[#/sec]?(mean)
Time?per?request:???????1.621?[ms]?(mean)
Time?per?request:???????1.621?[ms]?(mean,?across?all?concurrent?requests)
Transfer?rate:??????????509.16?[Kbytes/sec]?received
Connection?Times?(ms)
??????????????min??mean[+/-sd]?median???max
Connect:????????0????1???0.3??????0???????1
Processing:?????1????1???0.3??????1???????2
Waiting:????????0????1???0.3??????1???????1
Total:??????????1????1???0.5??????1???????2
ERROR:?The?median?and?mean?for?the?initial?connection?time?are?more?than?twice?the?standard
???????deviation?apart.?These?results?are?NOT?reliable.
Percentage?of?the?requests?served?within?a?certain?time?(ms)
??50%??????1
??66%??????1
??75%??????1
??80%??????2
??90%??????2
??95%??????2
??98%??????2
??99%??????2
?100%??????2?(longest?request)
查看nginx日志
172.16.1.10
[root@localhost?~]#?tail?/usr/local/nginx/logs/access.log
172.16.1.100?-?-?[26/Jul/2020:05:58:24?+0800]?"GET?/?HTTP/1.0"?200?612?"-"?"ApacheBench/2.3"
172.16.1.100?-?-?[26/Jul/2020:05:58:24?+0800]?"GET?/?HTTP/1.0"?200?612?"-"?"ApacheBench/2.3"
172.16.1.100?-?-?[26/Jul/2020:05:58:24?+0800]?"GET?/?HTTP/1.0"?200?612?"-"?"ApacheBench/2.3"
172.16.1.100?-?-?[26/Jul/2020:05:58:24?+0800]?"GET?/?HTTP/1.0"?200?612?"-"?"ApacheBench/2.3"
172.16.1.100?-?-?[26/Jul/2020:05:58:24?+0800]?"GET?/?HTTP/1.0"?200?612?"-"?"ApacheBench/2.3"
172.16.1.100?-?-?[26/Jul/2020:05:58:24?+0800]?"GET?/?HTTP/1.0"?200?612?"-"?"ApacheBench/2.3"
172.16.1.100?-?-?[26/Jul/2020:05:58:24?+0800]?"GET?/?HTTP/1.0"?200?612?"-"?"ApacheBench/2.3"
172.16.1.100?-?-?[26/Jul/2020:05:58:24?+0800]?"GET?/?HTTP/1.0"?200?612?"-"?"ApacheBench/2.3"
172.16.1.100?-?-?[26/Jul/2020:05:58:24?+0800]?"GET?/?HTTP/1.0"?200?612?"-"?"ApacheBench/2.3"
172.16.1.100?-?-?[26/Jul/2020:05:58:24?+0800]?"GET?/?HTTP/1.0"?200?612?"-"?"ApacheBench/2.3"
由此可見(jiàn),一秒鐘之內(nèi)172.16.1.100訪問(wèn)了nginx10次,接下來(lái)禁止掉這個(gè)問(wèn)題ip
通過(guò)iptables限制ip訪問(wèn)
172.16.1.10
[root@localhost?~]#?iptables?-I?INPUT?-s?172.16.1.100?-ptcp?--dport?80?-j?DROP
172.16.1.100
[root@localhost?~]#?curl?172.16.1.10
curl:?(7)?Failed?connect?to?172.16.1.10:80;?連接超時(shí)
此時(shí)172.16.1.100再也不能訪問(wèn)nginx
nginx配置文件限制
172.16.1.10
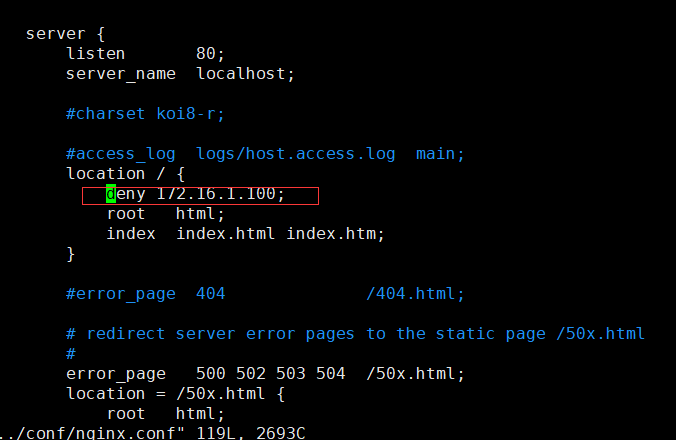
172.16.1.100
[root@localhost?~]#?curl?-I?172.16.1.10
HTTP/1.1?403?Forbidden
Server:?nginx/1.11.2
Date:?Sat,?25?Jul?2020?23:12:06?GMT
Content-Type:?text/html
Content-Length:?169
Connection:?keep-alive
<以上代碼可復(fù)制粘貼,可往左滑>
總? ? 結(jié)
以上就是兩種簡(jiǎn)單的方法限制ip訪問(wèn),還有許多方法可以利用工具進(jìn)行ip限制。
推薦閱讀:
5T技術(shù)資源大放送!包括但不限于:C/C++,Linux,Python,Java,PHP,人工智能,單片機(jī),樹(shù)莓派,等等。在公眾號(hào)內(nèi)回復(fù)「1024」,即可免費(fèi)獲取!!
評(píng)論
圖片
表情
