SpringSecurity + JWT 實(shí)現(xiàn)單點(diǎn)登錄
本文我們來看下 SpringSecurity + JWT 實(shí)現(xiàn)單點(diǎn)登錄操作,本文 2W 字,預(yù)計(jì)閱讀時間 30 min,文章提供了代碼骨架,建議收藏。
單點(diǎn)登錄(Single Sign On),簡稱為 SSO,是目前比較流行的企業(yè)業(yè)務(wù)整合的解決方案之一。SSO的定義是在多個應(yīng)用系統(tǒng)中,用戶只需要登錄一次就可以訪問所有相互信任的應(yīng)用系統(tǒng)
二、簡單的運(yùn)行機(jī)制
單點(diǎn)登錄的機(jī)制其實(shí)是比較簡單的,用一個現(xiàn)實(shí)中的例子做比較。某公園內(nèi)部有許多獨(dú)立的景點(diǎn),游客可以在各個景點(diǎn)門口單獨(dú)買票。
對于需要游玩所有的景點(diǎn)的游客,這種買票方式很不方便,需要在每個景點(diǎn)門口排隊(duì)買票,錢包拿 進(jìn)拿出的,容易丟失,很不安全。
于是絕大多數(shù)游客選擇在大門口買一張通票(也叫套票),就可以玩遍所有的景點(diǎn)而不需要重新再買票。他們只需要在每個景點(diǎn)門 口出示一下剛才買的套票就能夠被允許進(jìn)入每個獨(dú)立的景點(diǎn)。
單點(diǎn)登錄的機(jī)制也一樣,如下圖所示,
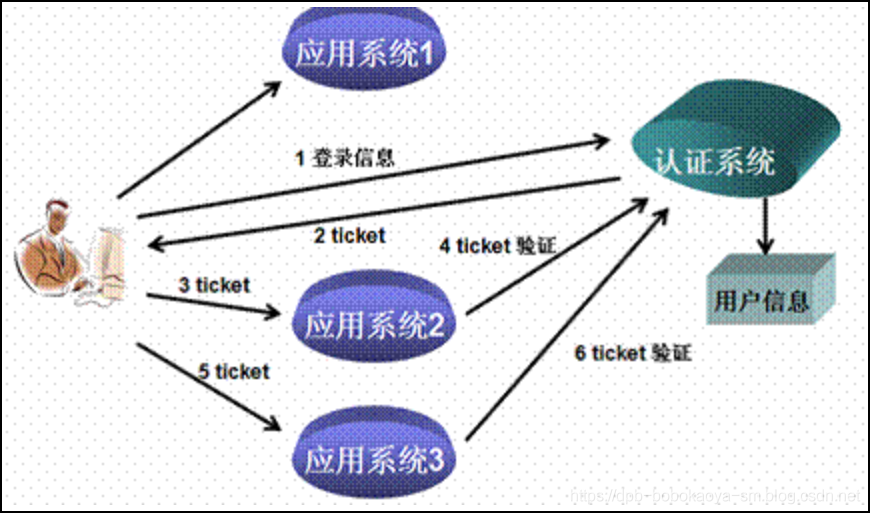
用戶認(rèn)證:這一環(huán)節(jié)主要是用戶向認(rèn)證服務(wù)器發(fā)起認(rèn)證請求,認(rèn)證服務(wù)器給用戶返回一個成功的令牌token,主要在認(rèn)證服務(wù)器中完成,即圖中的認(rèn)證系統(tǒng),注意認(rèn)證系統(tǒng)只能有一個。
身份校驗(yàn): 這一環(huán)節(jié)是用戶攜帶token去訪問其他服務(wù)器時,在其他服務(wù)器中要對token的真?zhèn)芜M(jìn)行檢驗(yàn),主要在資源服務(wù)器中完成,即圖中的應(yīng)用系統(tǒng)2 3
三、JWT介紹
概念說明
從分布式認(rèn)證流程中,我們不難發(fā)現(xiàn),這中間起最關(guān)鍵作用的就是token,token的安全與否,直接關(guān)系到系統(tǒng)的健壯性,這里我們選擇使用JWT來實(shí)現(xiàn)token的生成和校驗(yàn)。
JWT,全稱JSON Web Token,官網(wǎng)地址https://jwt.io,是一款出色的分布式身份校驗(yàn)方案。可以生成token,也可以解析檢驗(yàn)token。
JWT生成的token由三部分組成:
頭部:主要設(shè)置一些規(guī)范信息,簽名部分的編碼格式就在頭部中聲明。
載荷:token中存放有效信息的部分,比如用戶名,用戶角色,過期時間等,但是不要放密碼,會泄露!
簽名:將頭部與載荷分別采用base64編碼后,用“.”相連,再加入鹽,最后使用頭部聲明的編碼類型進(jìn)行編碼,就得到了簽名。
JWT生成token的安全性分析
從JWT生成的token組成上來看,要想避免token被偽造,主要就得看簽名部分了,而簽名部分又有三部分組成,其中頭部和載荷的base64編碼,幾乎是透明的,毫無安全性可言,那么最終守護(hù)token安全的重?fù)?dān)就落在了加入的鹽上面了!
試想:如果生成token所用的鹽與解析token時加入的鹽是一樣的。豈不是類似于中國人民銀行把人民幣防偽技術(shù)公開了?大家可以用這個鹽來解析token,就能用來偽造token。這時,我們就需要對鹽采用非對稱加密的方式進(jìn)行加密,以達(dá)到生成token與校驗(yàn)token方所用的鹽不一致的安全效果!
非對稱加密RSA介紹
基本原理:同時生成兩把密鑰:私鑰和公鑰,私鑰隱秘保存,公鑰可以下發(fā)給信任客戶端
私鑰加密,持有私鑰或公鑰才可以解密
公鑰加密,持有私鑰才可解密
優(yōu)點(diǎn): 安全,難以破解
缺點(diǎn): 算法比較耗時,為了安全,可以接受
歷史: 三位數(shù)學(xué)家Rivest、Shamir 和 Adleman 設(shè)計(jì)了一種算法,可以實(shí)現(xiàn)非對稱加密。這種算法用他們?nèi)齻€人的名字縮寫:RSA。
四、SpringSecurity整合JWT
1.認(rèn)證思路分析
SpringSecurity主要是通過過濾器來實(shí)現(xiàn)功能的!我們要找到SpringSecurity實(shí)現(xiàn)認(rèn)證和校驗(yàn)身份的過濾器!
回顧集中式認(rèn)證流程
用戶認(rèn)證:使用UsernamePasswordAuthenticationFilter過濾器中attemptAuthentication方法實(shí)現(xiàn)認(rèn)證功能,該過濾器父類中successfulAuthentication方法實(shí)現(xiàn)認(rèn)證成功后的操作。
身份校驗(yàn):使用BasicAuthenticationFilter過濾器中doFilterInternal方法驗(yàn)證是否登錄,以決定能否進(jìn)入后續(xù)過濾器。
分析分布式認(rèn)證流程
用戶認(rèn)證:
由于分布式項(xiàng)目,多數(shù)是前后端分離的架構(gòu)設(shè)計(jì),我們要滿足可以接受異步post的認(rèn)證請求參數(shù),需要修改UsernamePasswordAuthenticationFilter過濾器中attemptAuthentication方法,讓其能夠接收請求體。
另外,默認(rèn)successfulAuthentication方法在認(rèn)證通過后,是把用戶信息直接放入session就完事了,現(xiàn)在我們需要修改這個方法,在認(rèn)證通過后生成token并返回給用戶。
身份校驗(yàn):
原來BasicAuthenticationFilter過濾器中doFilterInternal方法校驗(yàn)用戶是否登錄,就是看session中是否有用戶信息,我們要修改為,驗(yàn)證用戶攜帶的token是否合法,并解析出用戶信息,交給SpringSecurity,以便于后續(xù)的授權(quán)功能可以正常使用。
2.具體實(shí)現(xiàn)
為了演示單點(diǎn)登錄的效果,我們設(shè)計(jì)如下項(xiàng)目結(jié)構(gòu)
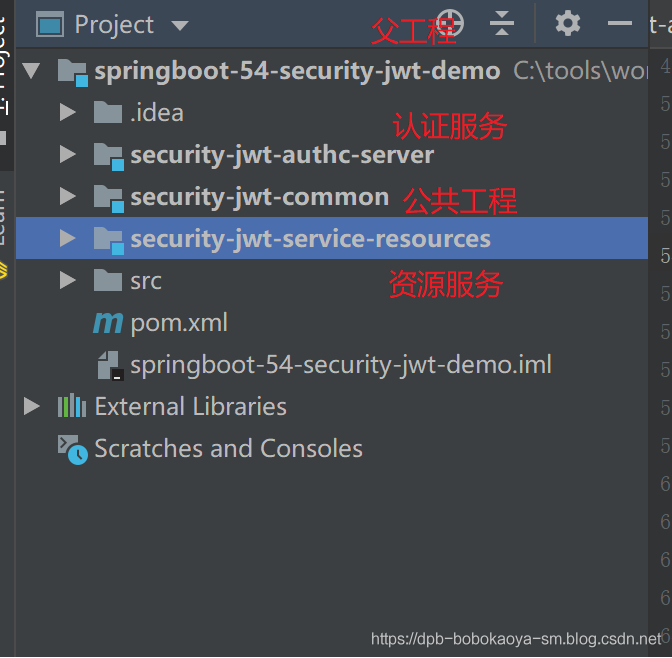
2.1父工程創(chuàng)建
因?yàn)楸景咐枰獎?chuàng)建多個系統(tǒng),所以我們使用maven聚合工程來實(shí)現(xiàn),首先創(chuàng)建一個父工程,導(dǎo)入springboot的父依賴即可
<parent>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-parent</artifactId>
<version>2.1.3.RELEASE</version>
<relativePath/>
</parent>2.2公共工程創(chuàng)建
然后創(chuàng)建一個common工程,其他工程依賴此系統(tǒng)
導(dǎo)入JWT相關(guān)的依賴
<dependencies>
<dependency>
<groupId>io.jsonwebtoken</groupId>
<artifactId>jjwt-api</artifactId>
<version>0.10.7</version>
</dependency>
<dependency>
<groupId>io.jsonwebtoken</groupId>
<artifactId>jjwt-impl</artifactId>
<version>0.10.7</version>
<scope>runtime</scope>
</dependency>
<dependency>
<groupId>io.jsonwebtoken</groupId>
<artifactId>jjwt-jackson</artifactId>
<version>0.10.7</version>
<scope>runtime</scope>
</dependency>
<!--jackson包-->
<dependency>
<groupId>com.fasterxml.jackson.core</groupId>
<artifactId>jackson-databind</artifactId>
<version>2.9.9</version>
</dependency>
<!--日志包-->
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-logging</artifactId>
</dependency>
<dependency>
<groupId>joda-time</groupId>
<artifactId>joda-time</artifactId>
</dependency>
<dependency>
<groupId>org.projectlombok</groupId>
<artifactId>lombok</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
</dependency>
</dependencies>創(chuàng)建相關(guān)的工具類
@Data
public class Payload <T>{
private String id;
private T userInfo;
private Date expiration;
}JsonUtils
public class JsonUtils {
public static final ObjectMapper mapper = new ObjectMapper();
private static final Logger logger = LoggerFactory.getLogger(JsonUtils.class);
public static String toString(Object obj) {
if (obj == null) {
return null;
}
if (obj.getClass() == String.class) {
return (String) obj;
}
try {
return mapper.writeValueAsString(obj);
} catch (JsonProcessingException e) {
logger.error("json序列化出錯:" + obj, e);
return null;
}
}
public static <T> T toBean(String json, Class<T> tClass) {
try {
return mapper.readValue(json, tClass);
} catch (IOException e) {
logger.error("json解析出錯:" + json, e);
return null;
}
}
public static <E> List<E> toList(String json, Class<E> eClass) {
try {
return mapper.readValue(json, mapper.getTypeFactory().constructCollectionType(List.class, eClass));
} catch (IOException e) {
logger.error("json解析出錯:" + json, e);
return null;
}
}
public static <K, V> Map<K, V> toMap(String json, Class<K> kClass, Class<V> vClass) {
try {
return mapper.readValue(json, mapper.getTypeFactory().constructMapType(Map.class, kClass, vClass));
} catch (IOException e) {
logger.error("json解析出錯:" + json, e);
return null;
}
}
public static <T> T nativeRead(String json, TypeReference<T> type) {
try {
return mapper.readValue(json, type);
} catch (IOException e) {
logger.error("json解析出錯:" + json, e);
return null;
}
}
}JwtUtils
public class JwtUtils {
private static final String JWT_PAYLOAD_USER_KEY = "user";
/**
* 私鑰加密token
*
* @param userInfo 載荷中的數(shù)據(jù)
* @param privateKey 私鑰
* @param expire 過期時間,單位分鐘
* @return JWT
*/
public static String generateTokenExpireInMinutes(Object userInfo, PrivateKey privateKey, int expire) {
return Jwts.builder()
.claim(JWT_PAYLOAD_USER_KEY, JsonUtils.toString(userInfo))
.setId(createJTI())
.setExpiration(DateTime.now().plusMinutes(expire).toDate())
.signWith(privateKey, SignatureAlgorithm.RS256)
.compact();
}
/**
* 私鑰加密token
*
* @param userInfo 載荷中的數(shù)據(jù)
* @param privateKey 私鑰
* @param expire 過期時間,單位秒
* @return JWT
*/
public static String generateTokenExpireInSeconds(Object userInfo, PrivateKey privateKey, int expire) {
return Jwts.builder()
.claim(JWT_PAYLOAD_USER_KEY, JsonUtils.toString(userInfo))
.setId(createJTI())
.setExpiration(DateTime.now().plusSeconds(expire).toDate())
.signWith(privateKey, SignatureAlgorithm.RS256)
.compact();
}
/**
* 公鑰解析token
*
* @param token 用戶請求中的token
* @param publicKey 公鑰
* @return Jws<Claims>
*/
private static Jws<Claims> parserToken(String token, PublicKey publicKey) {
return Jwts.parser().setSigningKey(publicKey).parseClaimsJws(token);
}
private static String createJTI() {
return new String(Base64.getEncoder().encode(UUID.randomUUID().toString().getBytes()));
}
/**
* 獲取token中的用戶信息
*
* @param token 用戶請求中的令牌
* @param publicKey 公鑰
* @return 用戶信息
*/
public static <T> Payload<T> getInfoFromToken(String token, PublicKey publicKey, Class<T> userType) {
Jws<Claims> claimsJws = parserToken(token, publicKey);
Claims body = claimsJws.getBody();
Payload<T> claims = new Payload<>();
claims.setId(body.getId());
claims.setUserInfo(JsonUtils.toBean(body.get(JWT_PAYLOAD_USER_KEY).toString(), userType));
claims.setExpiration(body.getExpiration());
return claims;
}
/**
* 獲取token中的載荷信息
*
* @param token 用戶請求中的令牌
* @param publicKey 公鑰
* @return 用戶信息
*/
public static <T> Payload<T> getInfoFromToken(String token, PublicKey publicKey) {
Jws<Claims> claimsJws = parserToken(token, publicKey);
Claims body = claimsJws.getBody();
Payload<T> claims = new Payload<>();
claims.setId(body.getId());
claims.setExpiration(body.getExpiration());
return claims;
}
}RsaUtils
public class RsaUtils {
private static final int DEFAULT_KEY_SIZE = 2048;
/**
* 從文件中讀取公鑰
*
* @param filename 公鑰保存路徑,相對于classpath
* @return 公鑰對象
* @throws Exception
*/
public static PublicKey getPublicKey(String filename) throws Exception {
byte[] bytes = readFile(filename);
return getPublicKey(bytes);
}
/**
* 從文件中讀取密鑰
*
* @param filename 私鑰保存路徑,相對于classpath
* @return 私鑰對象
* @throws Exception
*/
public static PrivateKey getPrivateKey(String filename) throws Exception {
byte[] bytes = readFile(filename);
return getPrivateKey(bytes);
}
/**
* 獲取公鑰
*
* @param bytes 公鑰的字節(jié)形式
* @return
* @throws Exception
*/
private static PublicKey getPublicKey(byte[] bytes) throws Exception {
bytes = Base64.getDecoder().decode(bytes);
X509EncodedKeySpec spec = new X509EncodedKeySpec(bytes);
KeyFactory factory = KeyFactory.getInstance("RSA");
return factory.generatePublic(spec);
}
/**
* 獲取密鑰
*
* @param bytes 私鑰的字節(jié)形式
* @return
* @throws Exception
*/
private static PrivateKey getPrivateKey(byte[] bytes) throws NoSuchAlgorithmException, InvalidKeySpecException {
bytes = Base64.getDecoder().decode(bytes);
PKCS8EncodedKeySpec spec = new PKCS8EncodedKeySpec(bytes);
KeyFactory factory = KeyFactory.getInstance("RSA");
return factory.generatePrivate(spec);
}
/**
* 根據(jù)密文,生存rsa公鑰和私鑰,并寫入指定文件
*
* @param publicKeyFilename 公鑰文件路徑
* @param privateKeyFilename 私鑰文件路徑
* @param secret 生成密鑰的密文
*/
public static void generateKey(String publicKeyFilename, String privateKeyFilename, String secret, int keySize) throws Exception {
KeyPairGenerator keyPairGenerator = KeyPairGenerator.getInstance("RSA");
SecureRandom secureRandom = new SecureRandom(secret.getBytes());
keyPairGenerator.initialize(Math.max(keySize, DEFAULT_KEY_SIZE), secureRandom);
KeyPair keyPair = keyPairGenerator.genKeyPair();
// 獲取公鑰并寫出
byte[] publicKeyBytes = keyPair.getPublic().getEncoded();
publicKeyBytes = Base64.getEncoder().encode(publicKeyBytes);
writeFile(publicKeyFilename, publicKeyBytes);
// 獲取私鑰并寫出
byte[] privateKeyBytes = keyPair.getPrivate().getEncoded();
privateKeyBytes = Base64.getEncoder().encode(privateKeyBytes);
writeFile(privateKeyFilename, privateKeyBytes);
}
private static byte[] readFile(String fileName) throws Exception {
return Files.readAllBytes(new File(fileName).toPath());
}
private static void writeFile(String destPath, byte[] bytes) throws IOException {
File dest = new File(destPath);
if (!dest.exists()) {
dest.createNewFile();
}
Files.write(dest.toPath(), bytes);
}
}在通用子模塊中編寫測試類生成rsa公鑰和私鑰
public class JwtTest {
private String privateKey = "c:/tools/auth_key/id_key_rsa";
private String publicKey = "c:/tools/auth_key/id_key_rsa.pub";
@Test
public void test1() throws Exception{
RsaUtils.generateKey(publicKey,privateKey,"dpb",1024);
}
}
2.3認(rèn)證系統(tǒng)創(chuàng)建
接下來我們創(chuàng)建我們的認(rèn)證服務(wù)。
導(dǎo)入相關(guān)的依賴
<dependencies>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-security</artifactId>
</dependency>
<dependency>
<artifactId>security-jwt-common</artifactId>
<groupId>com.dpb</groupId>
<version>1.0-SNAPSHOT</version>
</dependency>
<dependency>
<groupId>mysql</groupId>
<artifactId>mysql-connector-java</artifactId>
<version>5.1.47</version>
</dependency>
<dependency>
<groupId>org.mybatis.spring.boot</groupId>
<artifactId>mybatis-spring-boot-starter</artifactId>
<version>2.1.0</version>
</dependency>
<dependency>
<groupId>com.alibaba</groupId>
<artifactId>druid</artifactId>
<version>1.1.10</version>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-configuration-processor</artifactId>
<optional>true</optional>
</dependency>
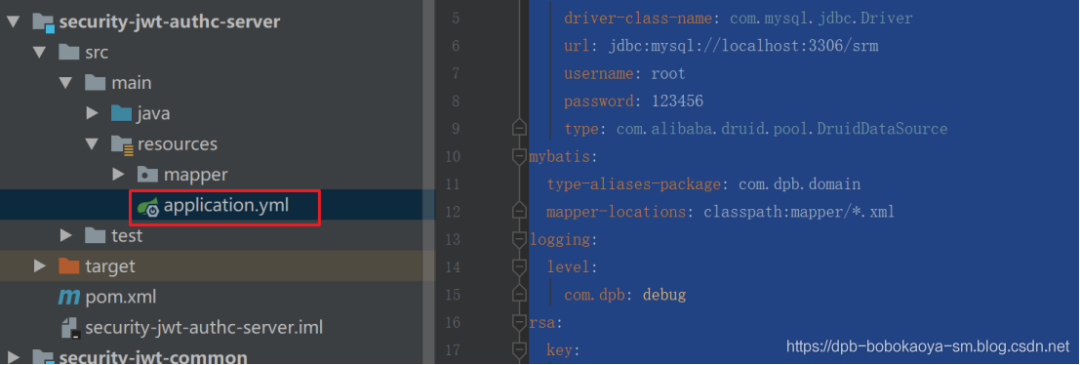
</dependencies>創(chuàng)建配置文件
spring:
datasource:
driver-class-name: com.mysql.jdbc.Driver
url: jdbc:mysql://localhost:3306/srm
username: root
password: 123456
type: com.alibaba.druid.pool.DruidDataSource
mybatis:
type-aliases-package: com.dpb.domain
mapper-locations: classpath:mapper/*.xml
logging:
level:
com.dpb: debug
rsa:
key:
pubKeyFile: c:\tools\auth_key\id_key_rsa.pub
priKeyFile: c:\tools\auth_key\id_key_rsa
提供公鑰私鑰的配置類
@Data
@ConfigurationProperties(prefix = "rsa.key")
public class RsaKeyProperties {
private String pubKeyFile;
private String priKeyFile;
private PublicKey publicKey;
private PrivateKey privateKey;
/**
* 系統(tǒng)啟動的時候觸發(fā)
* @throws Exception
*/
@PostConstruct
public void createRsaKey() throws Exception {
publicKey = RsaUtils.getPublicKey(pubKeyFile);
privateKey = RsaUtils.getPrivateKey(priKeyFile);
}
}創(chuàng)建啟動類
@SpringBootApplication
@MapperScan("com.dpb.mapper")
@EnableConfigurationProperties(RsaKeyProperties.class)
public class App {
public static void main(String[] args) {
SpringApplication.run(App.class,args);
}
}完成數(shù)據(jù)認(rèn)證的邏輯
pojo
@Data
public class RolePojo implements GrantedAuthority {
private Integer id;
private String roleName;
private String roleDesc;
@JsonIgnore
@Override
public String getAuthority() {
return roleName;
}
}@Data
public class UserPojo implements UserDetails {
private Integer id;
private String username;
private String password;
private Integer status;
private List<RolePojo> roles;
@JsonIgnore
@Override
public Collection<? extends GrantedAuthority> getAuthorities() {
List<SimpleGrantedAuthority> auth = new ArrayList<>();
auth.add(new SimpleGrantedAuthority("ADMIN"));
return auth;
}
@Override
public String getPassword() {
return this.password;
}
@Override
public String getUsername() {
return this.username;
}
@JsonIgnore
@Override
public boolean isAccountNonExpired() {
return true;
}
@JsonIgnore
@Override
public boolean isAccountNonLocked() {
return true;
}
@JsonIgnore
@Override
public boolean isCredentialsNonExpired() {
return true;
}
@JsonIgnore
@Override
public boolean isEnabled() {
return true;
}
}public interface UserMapper {
public UserPojo queryByUserName(@Param("userName") String userName);
}<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE mapper
PUBLIC "-//mybatis.org//DTD Mapper 3.0//EN"
"http://mybatis.org/dtd/mybatis-3-mapper.dtd">
<mapper namespace="com.dpb.mapper.UserMapper">
<select id="queryByUserName" resultType="UserPojo">
select * from t_user where username = #{userName}
</select>
</mapper>public interface UserService extends UserDetailsService {
}@Service
@Transactional
public class UserServiceImpl implements UserService {
@Autowired
private UserMapper mapper;
@Override
public UserDetails loadUserByUsername(String s) throws UsernameNotFoundException {
UserPojo user = mapper.queryByUserName(s);
return user;
}
}public class TokenLoginFilter extends UsernamePasswordAuthenticationFilter {
private AuthenticationManager authenticationManager;
private RsaKeyProperties prop;
public TokenLoginFilter(AuthenticationManager authenticationManager, RsaKeyProperties prop) {
this.authenticationManager = authenticationManager;
this.prop = prop;
}
public Authentication attemptAuthentication(HttpServletRequest request, HttpServletResponse response) throws AuthenticationException {
try {
UserPojo sysUser = new ObjectMapper().readValue(request.getInputStream(), UserPojo.class);
UsernamePasswordAuthenticationToken authRequest = new UsernamePasswordAuthenticationToken(sysUser.getUsername(), sysUser.getPassword());
return authenticationManager.authenticate(authRequest);
}catch (Exception e){
try {
response.setContentType("application/json;charset=utf-8");
response.setStatus(HttpServletResponse.SC_UNAUTHORIZED);
PrintWriter out = response.getWriter();
Map resultMap = new HashMap();
resultMap.put("code", HttpServletResponse.SC_UNAUTHORIZED);
resultMap.put("msg", "用戶名或密碼錯誤!");
out.write(new ObjectMapper().writeValueAsString(resultMap));
out.flush();
out.close();
}catch (Exception outEx){
outEx.printStackTrace();
}
throw new RuntimeException(e);
}
}
public void successfulAuthentication(HttpServletRequest request, HttpServletResponse response, FilterChain chain, Authentication authResult) throws IOException, ServletException {
UserPojo user = new UserPojo();
user.setUsername(authResult.getName());
user.setRoles((List<RolePojo>)authResult.getAuthorities());
String token = JwtUtils.generateTokenExpireInMinutes(user, prop.getPrivateKey(), 24 * 60);
response.addHeader("Authorization", "Bearer "+token);
try {
response.setContentType("application/json;charset=utf-8");
response.setStatus(HttpServletResponse.SC_OK);
PrintWriter out = response.getWriter();
Map resultMap = new HashMap();
resultMap.put("code", HttpServletResponse.SC_OK);
resultMap.put("msg", "認(rèn)證通過!");
out.write(new ObjectMapper().writeValueAsString(resultMap));
out.flush();
out.close();
}catch (Exception outEx){
outEx.printStackTrace();
}
}
}自定義校驗(yàn)token的過濾器
public class TokenVerifyFilter extends BasicAuthenticationFilter {
private RsaKeyProperties prop;
public TokenVerifyFilter(AuthenticationManager authenticationManager, RsaKeyProperties prop) {
super(authenticationManager);
this.prop = prop;
}
public void doFilterInternal(HttpServletRequest request, HttpServletResponse response, FilterChain chain) throws IOException, ServletException {
String header = request.getHeader("Authorization");
if (header == null || !header.startsWith("Bearer ")) {
//如果攜帶錯誤的token,則給用戶提示請登錄!
chain.doFilter(request, response);
response.setContentType("application/json;charset=utf-8");
response.setStatus(HttpServletResponse.SC_FORBIDDEN);
PrintWriter out = response.getWriter();
Map resultMap = new HashMap();
resultMap.put("code", HttpServletResponse.SC_FORBIDDEN);
resultMap.put("msg", "請登錄!");
out.write(new ObjectMapper().writeValueAsString(resultMap));
out.flush();
out.close();
} else {
//如果攜帶了正確格式的token要先得到token
String token = header.replace("Bearer ", "");
//驗(yàn)證tken是否正確
Payload<UserPojo> payload = JwtUtils.getInfoFromToken(token, prop.getPublicKey(), UserPojo.class);
UserPojo user = payload.getUserInfo();
if(user!=null){
UsernamePasswordAuthenticationToken authResult = new UsernamePasswordAuthenticationToken(user.getUsername(), null, user.getAuthorities());
SecurityContextHolder.getContext().setAuthentication(authResult);
chain.doFilter(request, response);
}
}
}
}編寫SpringSecurity的配置類
@Configuration
@EnableWebSecurity
@EnableGlobalMethodSecurity(securedEnabled=true)
public class WebSecurityConfig extends WebSecurityConfigurerAdapter {
@Autowired
private UserService userService;
@Autowired
private RsaKeyProperties prop;
@Bean
public BCryptPasswordEncoder passwordEncoder(){
return new BCryptPasswordEncoder();
}
//指定認(rèn)證對象的來源
public void configure(AuthenticationManagerBuilder auth) throws Exception {
auth.userDetailsService(userService).passwordEncoder(passwordEncoder());
}
//SpringSecurity配置信息
public void configure(HttpSecurity http) throws Exception {
http.csrf()
.disable()
.authorizeRequests()
.antMatchers("/user/query").hasAnyRole("ADMIN")
.anyRequest()
.authenticated()
.and()
.addFilter(new TokenLoginFilter(super.authenticationManager(), prop))
.addFilter(new TokenVerifyFilter(super.authenticationManager(), prop))
.sessionManagement().sessionCreationPolicy(SessionCreationPolicy.STATELESS);
}
}啟動服務(wù)測試
啟動服務(wù)
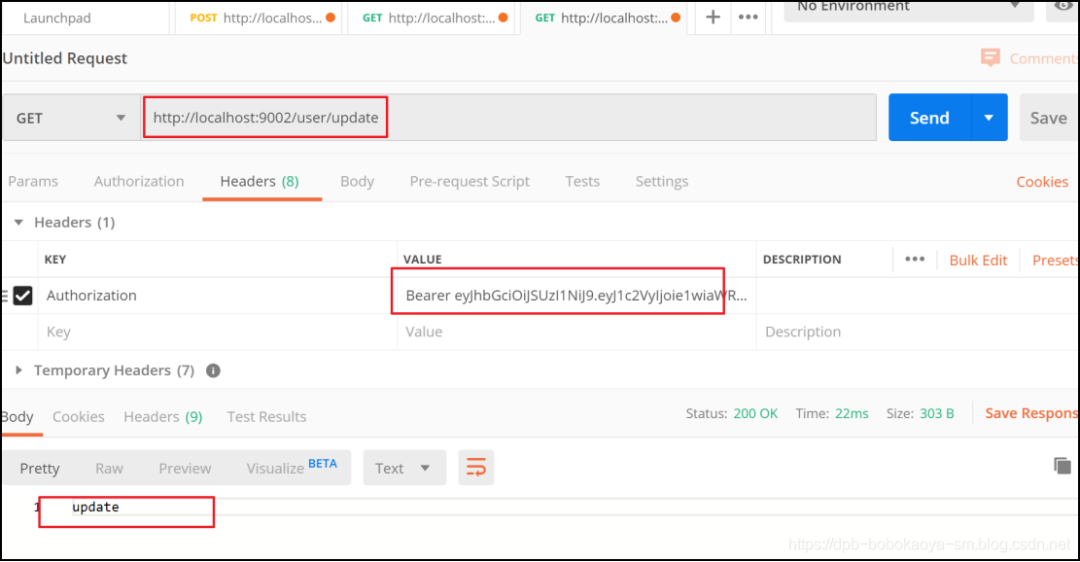
通過Postman來訪問測試
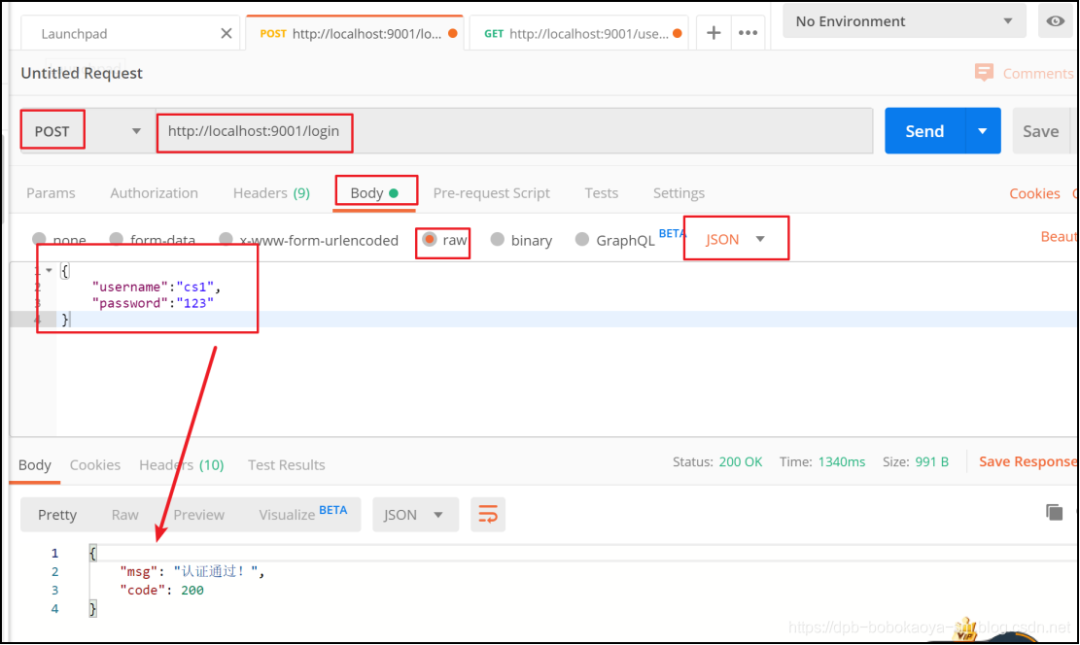
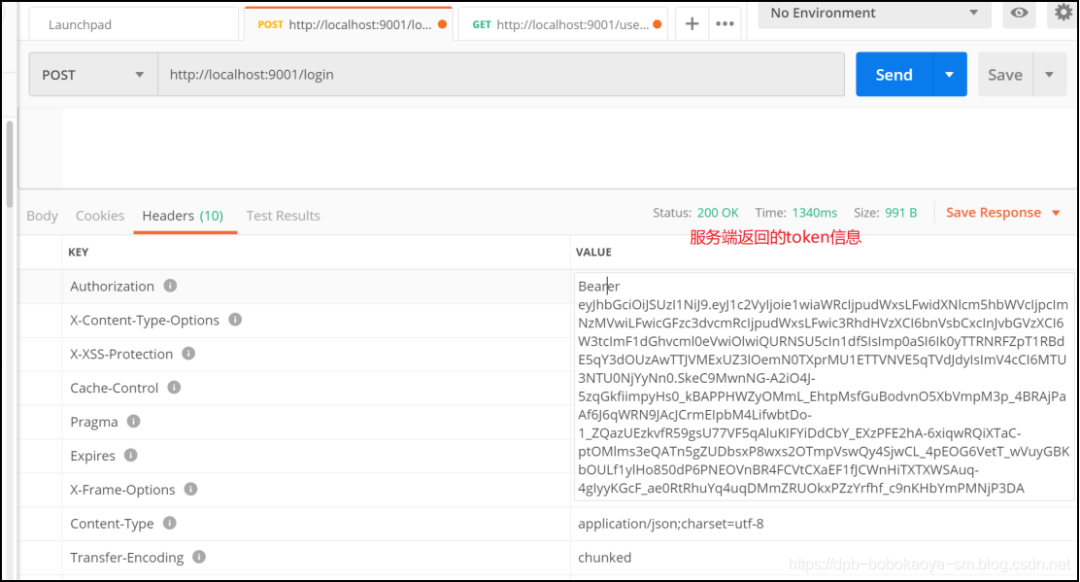
根據(jù)token信息我們訪問其他資源
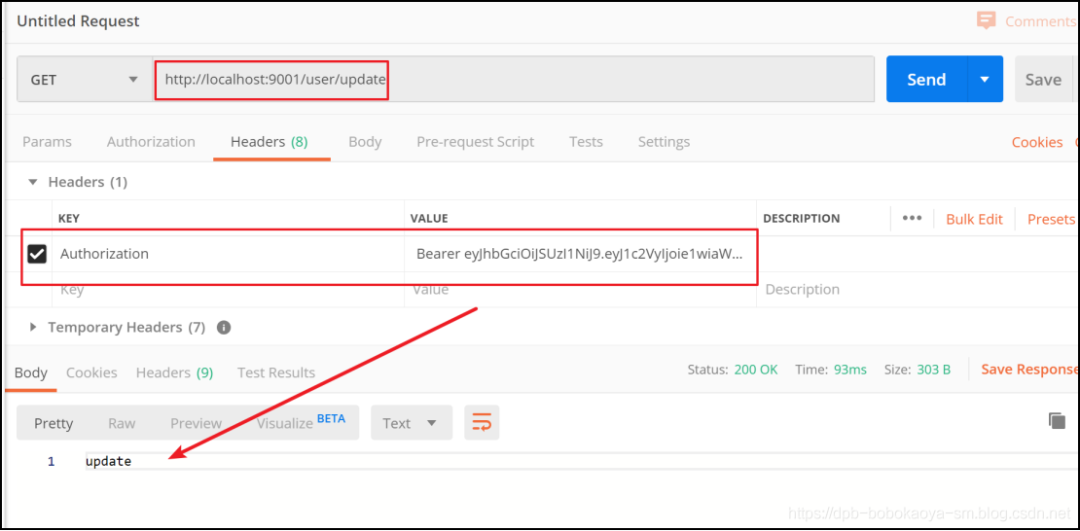
2.4資源系統(tǒng)創(chuàng)建
說明
資源服務(wù)可以有很多個,這里只拿產(chǎn)品服務(wù)為例,記住,資源服務(wù)中只能通過公鑰驗(yàn)證認(rèn)證。不能簽發(fā)token!創(chuàng)建產(chǎn)品服務(wù)并導(dǎo)入jar包根據(jù)實(shí)際業(yè)務(wù)導(dǎo)包即可,咱們就暫時和認(rèn)證服務(wù)一樣了。
接下來我們再創(chuàng)建一個資源服務(wù)
導(dǎo)入相關(guān)的依賴
<dependencies>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-security</artifactId>
</dependency>
<dependency>
<artifactId>security-jwt-common</artifactId>
<groupId>com.dpb</groupId>
<version>1.0-SNAPSHOT</version>
</dependency>
<dependency>
<groupId>mysql</groupId>
<artifactId>mysql-connector-java</artifactId>
<version>5.1.47</version>
</dependency>
<dependency>
<groupId>org.mybatis.spring.boot</groupId>
<artifactId>mybatis-spring-boot-starter</artifactId>
<version>2.1.0</version>
</dependency>
<dependency>
<groupId>com.alibaba</groupId>
<artifactId>druid</artifactId>
<version>1.1.10</version>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-configuration-processor</artifactId>
<optional>true</optional>
</dependency>
</dependencies>編寫產(chǎn)品服務(wù)配置文件
切記這里只能有公鑰地址!
server:
port: 9002
spring:
datasource:
driver-class-name: com.mysql.jdbc.Driver
url: jdbc:mysql://localhost:3306/srm
username: root
password: 123456
type: com.alibaba.druid.pool.DruidDataSource
mybatis:
type-aliases-package: com.dpb.domain
mapper-locations: classpath:mapper/*.xml
logging:
level:
com.dpb: debug
rsa:
key:
pubKeyFile: c:\tools\auth_key\id_key_rsa.pub編寫讀取公鑰的配置類
@Data
@ConfigurationProperties(prefix = "rsa.key")
public class RsaKeyProperties {
private String pubKeyFile;
private PublicKey publicKey;
/**
* 系統(tǒng)啟動的時候觸發(fā)
* @throws Exception
*/
@PostConstruct
public void createRsaKey() throws Exception {
publicKey = RsaUtils.getPublicKey(pubKeyFile);
}
}編寫啟動類
@SpringBootApplication
@MapperScan("com.dpb.mapper")
@EnableConfigurationProperties(RsaKeyProperties.class)
public class App {
public static void main(String[] args) {
SpringApplication.run(App.class,args);
}
}復(fù)制認(rèn)證服務(wù)中,用戶對象,角色對象和校驗(yàn)認(rèn)證的接口
復(fù)制認(rèn)證服務(wù)中的相關(guān)內(nèi)容即可
復(fù)制認(rèn)證服務(wù)中SpringSecurity配置類做修改
@Configuration
@EnableWebSecurity
@EnableGlobalMethodSecurity(securedEnabled=true)
public class WebSecurityConfig extends WebSecurityConfigurerAdapter {
@Autowired
private UserService userService;
@Autowired
private RsaKeyProperties prop;
@Bean
public BCryptPasswordEncoder passwordEncoder(){
return new BCryptPasswordEncoder();
}
//指定認(rèn)證對象的來源
public void configure(AuthenticationManagerBuilder auth) throws Exception {
auth.userDetailsService(userService).passwordEncoder(passwordEncoder());
}
//SpringSecurity配置信息
public void configure(HttpSecurity http) throws Exception {
http.csrf()
.disable()
.authorizeRequests()
//.antMatchers("/user/query").hasAnyRole("USER")
.anyRequest()
.authenticated()
.and()
.addFilter(new TokenVerifyFilter(super.authenticationManager(), prop))
// 禁用掉session
.sessionManagement().sessionCreationPolicy(SessionCreationPolicy.STATELESS);
}
}去掉“增加自定義認(rèn)證過濾器”即可!
編寫產(chǎn)品處理器
@RestController
@RequestMapping("/user")
public class UserController {
@RequestMapping("/query")
public String query(){
return "success";
}
@RequestMapping("/update")
public String update(){
return "update";
}
}
dpb-bobokaoya-sm.blog.csdn.net/article/details/103409430
推薦閱讀: 推薦7個牛哄哄 Spring Cloud 實(shí)戰(zhàn)項(xiàng)目 基于 SpringBoot + Vue 框架開發(fā)的網(wǎng)頁版聊天室項(xiàng)目 基于 SpringBoot + Vue 實(shí)現(xiàn)的可視化拖拽編輯的大屏項(xiàng)目 Github上10個超好看 可視化面板,后臺管理頁面有著落了 這可能是史上功能最全的Java權(quán)限認(rèn)證框架! 最近面試BAT,整理一份面試資料《Java面試BAT通關(guān)手冊》,覆蓋了Java核心技術(shù)、JVM、Java并發(fā)、SSM、微服務(wù)、數(shù)據(jù)庫、數(shù)據(jù)結(jié)構(gòu)等等。 獲取方式:關(guān)注公眾號并回復(fù) java 領(lǐng)取,更多內(nèi)容陸續(xù)奉上。 明天見(??ω??)??
